Download0 Screenshots
No review
Welcome to the official site of HijackThis.com. If you have been infected by a browser hijacker or similar malware threat, or are having other problems with your computer’s performance, we can help. Are there such things as Hijackthis programs for mac computers? KoolStar macrumors demi-god. Oct 16, 2006 825 9 Kentucky.
- HijackThis (also HiJackThis or HJT) is a free and open-source tool to detect malware and adware on Microsoft Windows. It was originally created by Merijn Bellekom, and later sold to Trend Micro. The program is notable for quickly scanning a user's computer to display the most common locations of malware, rather than relying on a database of.
- HijackThis 1.0.0. An essential tool to analize your PC configuration in depth. 4.2 (205 votes) 2.9.0.26 Stanislav Polshyn. Review Comments (17) Questions & Answers.
- As referenced in that guide is an outdated program that isnt' effective, people have moved on to OTL. There's just extra stuff there that I don't feel is necessary and it's less of a step-by-step guide.
HijackThis focuses on displaying browser hijacking locations, meaning it cannot detect and remove spyware, it simply delivers a list of most probable locations where browser hijacking can occur. The program does not separate information into good or bad so it is highly recommended to remove entries only if you are familiar with the presented information. HijackThis is a tool designed specifically for advanced users.
If you can’t interpret a HijackThis log on your own , ask a friend for help or contact members of the HijackThis online community, present on a large number of forums.
- License:
- Platform:
- Publisher:
- File size:
- Updated:
- User Rating:
- Editors' Review:
- Downloads:
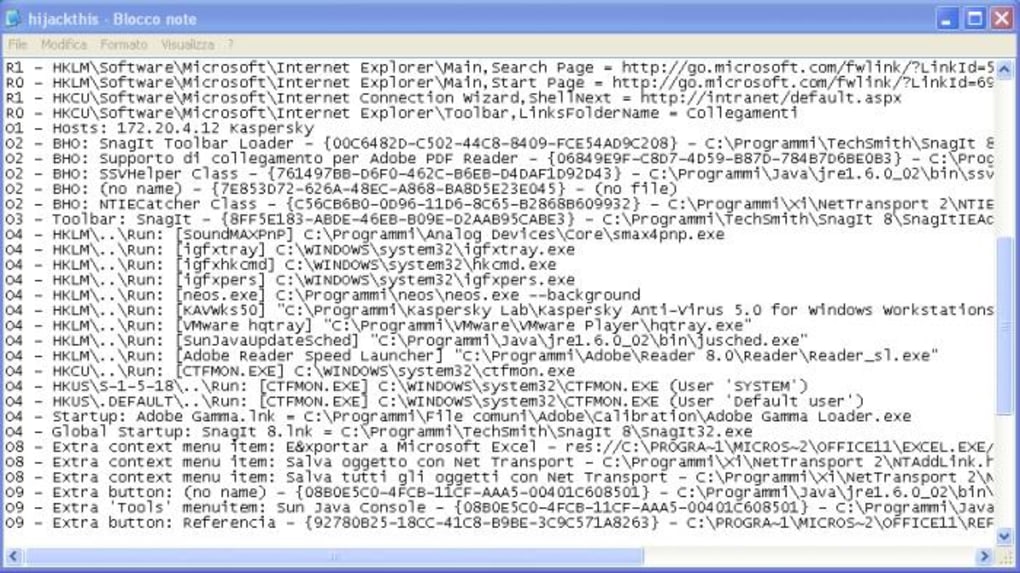
Most users with some experience of dealing with malware will have heard of the tool Trend Micro HijackThis. During the Windows XP era, the HiJackThis tool was most frequently being suggested to use for producing a detailed log file for analysis by experts from malware removal forums. If there are any anomalies detected on your computer via the log, you can easily be advised what to select for removal. After Trend Micro acquired HiJackThis, it’s unfortunate that it was never updated to fully work on Windows 7 as there are more checkpoints on newer Windows operating systems for malware to reside in.
The problem with HijackThis has always been that it’s not a tool for the inexperienced user because it doesn’t differentiate between malicious entries and those legitimately put there by software, so users have to rely on expert advice or risk making the computer worse by trying themselves. If you are the impatient type and want to quickly get some results about your log file without waiting for someone else to reply to you, here are 5 ways to automatically analyze the HiJackThis log file and quickly receive recommendations on what to fix.
Do note that the results and recommendations generated by these log analyzers are not always 100% accurate and are intended to be used for reference purposes so you can find out more information about suspect entries. Of course, you can try all 5 services to get more accurate results.
1. HijackThis.de Logfile AnalyzerHijackThis.de is one of the most well known and long running HijackThis analyzers and has a large database in recognizing if an entry is safe, unknown or nasty. You can either paste the log file into the text box or upload a log file from your computer, the option to show the visitor ratings is useful and should be left enabled. We got an “UPLOAD ERROR” when trying to upload the log file but it works fine when manually pasting the log content into the textbox.
The user ratings and scoring system are very handy when viewing the results because you can easily see what other people think about each entry in your log file, with the ability to also share your own ratings and opinions. Instead of having the long result, you can opt for short analysis at the end of the report. This will only display the entries that it advises you to do something about.
Visit HijackThis.de Logfile Analyzer
2. Help2Go Detective
Help2Go Detective is able analyze your HijackThis log file and gives some information about what it recommends you do with the malicious or suspicious objects. It also claims to detect over 12,000 malware signatures including the Peper and CoolWebSearch trojans.
Simply paste the HijackThis log file into the box and press the button. Unlike most of the other log analyzers, Help2Go Detective doesn’t list the whole log file contents and only the suspect objects along with some advice and suggestions such as booting into Safe Mode or updating Windows and your antivirus software.
Visit Help2Go Detective
3. Spy and Seek
Spy and Seek will analyze the log file you upload by clicking the Choose File button, then Analyze. You’ll get a display of the results in a traffic light type system of green for good, yellow for unknown and orange for known bad entries.
SpyAndSeek fully relies on the votes that it receives from registered members to determine the result of the process, and there are around 400,000 entries classified in its database, around 20,000 are known Bad ones. Clicking the Search column will link to a Google search for the entry or any comments left by other users, and there’s a useful URL for the results you can keep for future reference or share with more experienced users.
Visit Spy and Seek
4. ExeLib
The Exe Library is an online database that stores and lists executable files so you can check up on any suspicious processes. To use the HijackThis log Analyzer, just paste your log file into the box and click the Analyze button to get a report from ExeLib.
Any known or potentially malicious processes are shown in red, and you can get details of any known process by clicking on its hyperlink. We’re not quite sure how effective this tool is because all the other services flagged at least a few issues from some toolbars and home page hijackers in our log file but ExeLib listed no problems at all.
Visit ExeLib
5. Computer Hope Log Tool beta
We’re not sure how up to date the Computer Hope tool is, the last update announcement in the forum was 2011. Paste in your log file contents (ComboFix is also supported) and the results will show a great deal of information about all the objects with several different icons to represent the threat level, its type and whether it would be safe to remove.
Below the log result is a “Getting your system clean” section for what the tool recommends you do about the issues found including what steps to take in HijackThis or what files to delete. We would definitely advise seeking further information before removing what is listed because during testing it said to delete Skype and Flash files and remove Google Public DNS servers from our network adapter settings. A link to the report is found at the bottom of the page and will be available for a month.
Visit Computer Hope Log Tool beta
You might also like:
9 Automated Online Sandbox Services to Analyze Suspicious File’s Behavior3 Ways to Analyze Memory Dump (.dmp) File6 Tools to Analyze Programs that Auto Start in Windows8 Websites to Help Identify Good or Bad StartUp Programs6 Free Tools To Analyze Windows LNK Shortcut FilesCan someone please update this list please?
5 of the 6 listed/linked here are 404, only the last one ‘Computer Hope Log Tool beta” works, for now anyway.
Thanks!
Hello ! Still waiting . . . .
 Reply
Reply
Thank you for this very helpfull page. I have made a great clean-up in my HiJack log thanks to these analysers.
:-)
JiCé from France
hijackthis.co Use it all the time.
ReplyThank you all are great and useful tools
ReplyThanks for the details on sites for Hijackthis-had a few issues,but resolved(hopefully!)
All the best….
Hijackthis Mac
ReplyHijackthis For Mac
very helpful!
Replygreat! nice software! thanks a lot! :D